Vulnerability Scan and Pentest are often confused as the same service, but the reality is that we often acquire one but need the other. Both are important in their respective areas, necessary in an Information Security risk analysis and essential to ensure standards such as ISO 27001, CIS, NIST and others.
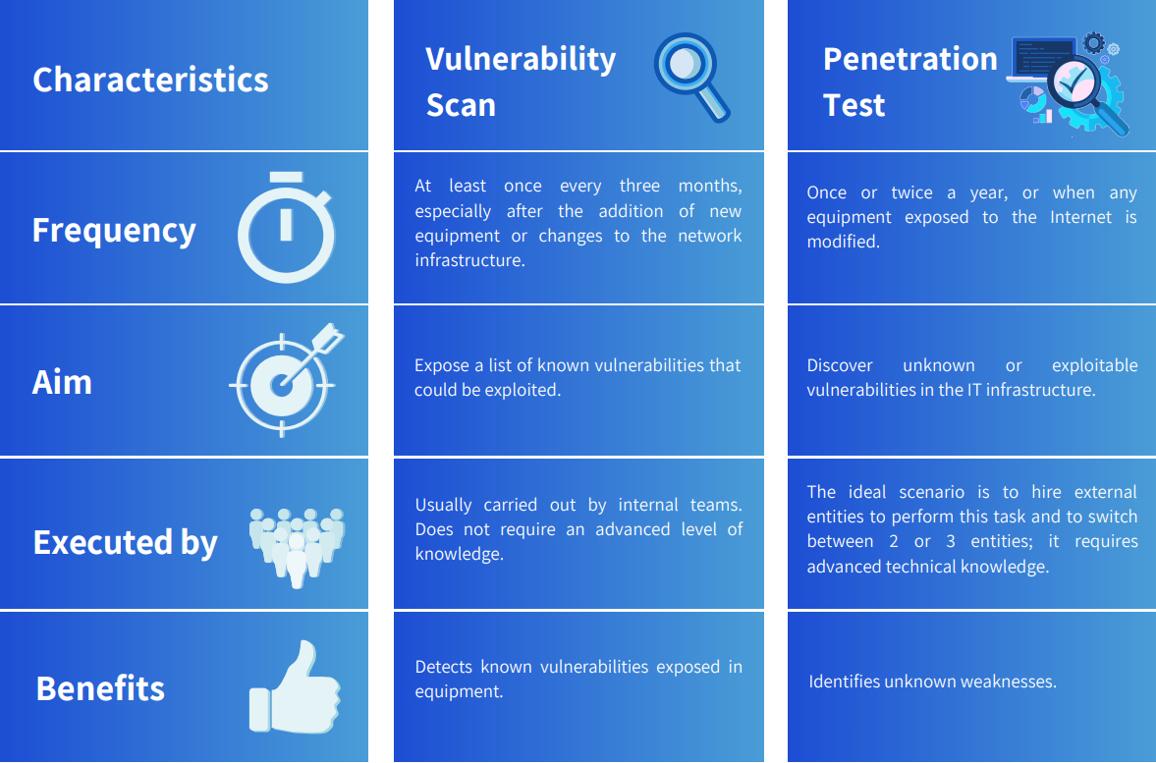
- Vulnerability Scan – The vulnerability scan is an autonomous process, which carries out tests and reports potential vulnerabilities in the IT infrastructure.
- Penetration Test – A penetration test is a thorough examination carried out to detect and exploit weaknesses and defects in the IT infrastructure
Both rely on three factors:
- Scope
- Criticality of Assets
- Cost and Risk
Vulnerability Scan
Vulnerability scanning is the act of identifying potential vulnerabilities of network devices such as firewalls, routers, switches, servers and applications. It is an automated process focused on finding potential and known vulnerabilities in the network or at an application level. Vulnerability scanners only identify potential vulnerabilities. As such, they are not designed to locate zero-day exploits. The scope of a vulnerability scan covers the entire organisation and uses automated tools to manage a large number of assets.
Its scope is broader than penetration testing. Expert knowledge of the solutions is fundamental to effectively use the vulnerability analysis tool. It is usually carried out by administrators or security teams with network training. Vulnerability scans can be performed frequently, on any number of assets, to verify if known vulnerabilities can be detected and fixed. That way, the most dangerous vulnerabilities in the most valuable resources can be quickly eliminated.
An efficient way to mitigate them is to follow the vulnerability management lifecycle. The cost of an analysis can be considered low or moderate compared to penetration tests, and it is a detection control rather than a preventive penetration test.
Vulnerability scans can be used by patch management for effective patch deployment. These patches should be tested on a test system before being deployed in production.
Penetration Tests
Comparatively, the scope of penetration testing is targeted and may involve the human factor. There is no automated penetration test. Therefore, it requires the use of a vast number of specialised tools. Also, it requires an extremely experienced professional to conduct it. An outstanding specialist always, at some point during a test, creates a script, changes the attack parameters or adjusts the settings of the tools used.
The test may be performed at application or network level, but is specific to a function, department or number of assets. It is possible to include the entire infrastructure and all applications, but this is an impractical option in the real world due to its cost and time. Its scope is defined based on a number of factors, which are based primarily on the risk and significance of an asset. Making a large investment in low-risk assets, which may take several days to exploit, is not practical. Penetration tests require highly qualified and skilled professionals and are, therefore, expensive. Penetration test specialists often exploit a new vulnerability or discover vulnerabilities that are not easily identified by normal organisational processes. Penetration tests can typically take days or even a few weeks to complete. They are often conducted once a year and the reports are short and objective. These tests are more likely than expected to cause disruptions.
Conclusion
Both the vulnerability scan and penetration test can contribute to the Information Security risk analysis process and help determine the most appropriate security policies for the organisation, department or process. All are used to reduce or mitigate Cybersecurity risks. It is necessary to differentiate between them, since both are relevant, with different purposes and outcomes.
Training is also crucial. Just giving security teams the tools does not mean the environment is safe. Lack of training in the proper use of tools poses a considerable security risk. In-depth knowledge of the solutions will bring an ROI in terms of quality, as well as a clear vision of the organisation’s security approach and a reduction of costs/time spent on unnecessary troubleshooting.