This article seeks to define and explain some common acronyms involved in today’s cybersecurity landscape.
What is UBA?
UBA stands for User Behaviour Analytics and is a threat detection analysis technology. UBA uses Artificial Intelligence (AI) and data science to understand how users normally behave and then find anomalous activities, which deviate from their normal behaviour and may be indicative of a threat.
How it works:
UBA seeks to understand the normal behaviour of all users in an environment and creates a baseline for that behaviour. How does this happen? It happens by using data science to build a behavioural model for every attribute of a user interacting with an IT environment.
Assume we want to model the VPN usage of user “Edson”. We could start by tracking various attributes of his VPN usage, including things like the start and end times of his VPN sessions, the IP addresses he connects from, from which country he connects, etc. For each of these attributes, we can build a model simply by recording his usage and analysing it with data science.
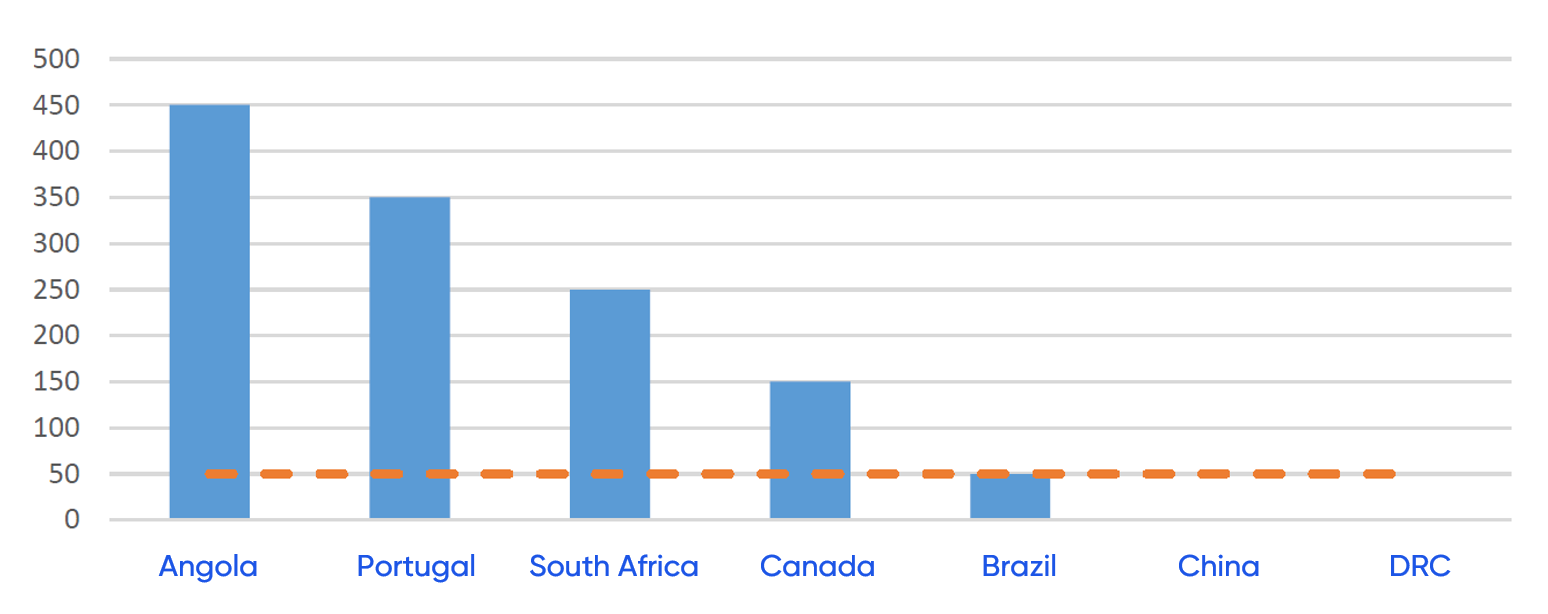
Let us suppose we are building a model for the countries where Edson’s VPNs are located. Each time he connects, we plot a data point.
Once we have enough data, data science can be used to identify trends in his VPN usage and understand what is a normal activity for him. Conceptually speaking, this data can be used to create a graph like the following:
VPN access: user “Edson”
Once a baseline for a normal activity has been established, the UBA can easily identify abnormal activity. Looking again at the graph above, the orange line represents his behavioural threshold; using the VPN from Angola, Portugal or South Africa would be normal for Edson, however, anything below that threshold would be abnormal. In this example, Brazil is at the limit, but it is still considered normal for him. Any VPN connection from a country Edson connects from less frequently than Brazil would be anomalous and would add risk points.
Risk scoring reduces false positives
Another core concept common to UBA solutions is the use of risk scores, instead of individual security alerts. In UBA, a single abnormality is not enough for an incident to be referred to analysts for review. Each behavioural abnormality discovered adds risk to the user. Once a user has enough risk points in a specific time period, that user is considered notable or high-risk. This approach reduces false positives because multiple abnormalities must occur before an analyst is alerted.
What is UEBA?
UEBA is exactly what it appears to be: UBA with an “E” in the middle of it. That “E” stands for Entities, which forms the new acronym User and Entity Behaviour Analytics. What this means is that UEBA is able to model the behaviour of users and also of machines within the network. Looking at it from a global perspective, this means that every IT environment is an interconnected network of users and machines, where UEBA can identify normal and abnormal behaviour for both groups providing complete visibility.
Uncovering machines with bad behaviour
UEBA acts by analysing the first time a machine executes an abnormal process or a known process running in an unusual location.
We will now look at a real-world example we discovered at a large US-based technology company. The security incident they experienced involved a Linux server that was compromised and controlled by hackers. The hackers were basically using that machine as a starting point to scan the rest of the network to find vulnerable assets with the intention of compromising those machines. The hackers scanned the network and its assets and then attempted to log into various servers using the default credentials of those servers.
In this example, there were many behavioural abnormalities, but they were all associated with one entity: a specific IP address. Without the ability to track and model entity behaviour, this attack would have gone undetected because the attack attempted to use many users (the default credentials) on multiple hosts. If the behavioural analysis was only being performed at the user level, this attack would have shown up as multiple users on different systems being unable to log. The fact that it was the same entity that performed the logins was what triggered it to be defined as an attack, and the ability to set the baseline and identify the unusual machine behaviour was what allowed the compromised machine to be discovered quickly before more damage could be done.
What is a SIEM?
SIEM stands for Security Information and Event Management. A SIEM solution allows events generated by various security applications (such as firewalls, proxies, intrusion prevention systems (IPS) and antivirus, among others) to be collected, standardised, stored and correlated; this enables rapid incident identification and response.
The original premise of SIEM was to help security teams collect and store event and log data, as well as, correlate that data to find threats. They are also used for compliance and reporting for companies that must adhere to compliance regulations such as GDPR, PCI-DSS and others.
SIEM Components
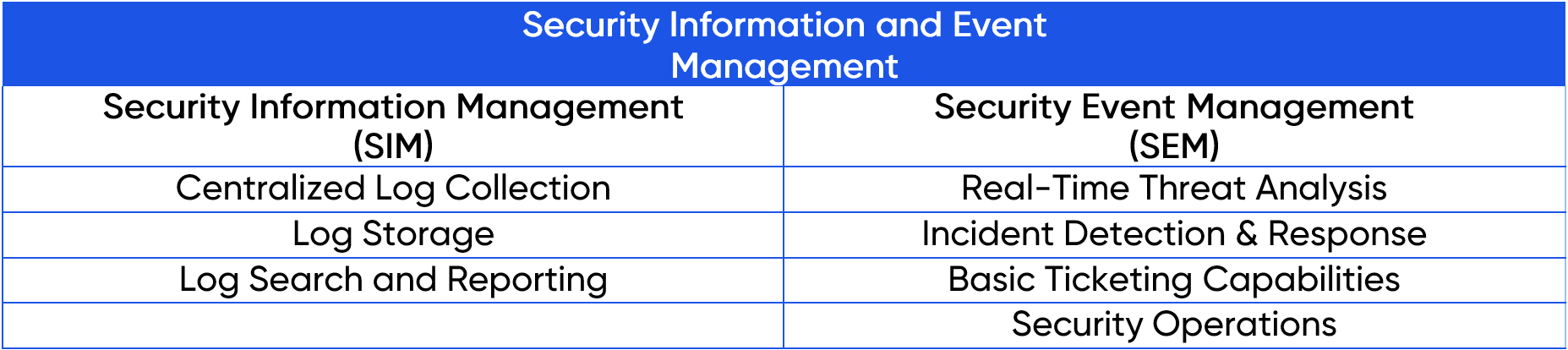
If we dissect the name, we can see that SIEM is a fusion of two other technologies: Security Information Management and Security Event Management.
In conclusion, Security Information Management (SIM) consists in bringing data together in one place and managing it efficiently. SIM includes the components that provide centralised log collection, log storage, log search and reporting, that enable compliance use cases.
Security Event Management (SEM) is a collection of features that enable threat detection and incident management use cases. These are things like real-time analysis and the use of correlation rules for incident detection. SEM also includes operational and response features such as incident management, which provides ticketing and security operation functionality.
The analogy of a needle in a haystack
People often try to explain SIEMs using the analogy “they help find needles in the haystack”. To be more precise, if event logs were hay, SIEMs would be responsible for collecting that hay (log collection and storage) and also finding the needles in that haystack (real-time threat detection, incident detection and response, etc.). While this is a great analogy to explain a SIEM, it is worth noting that SIEMs do a much better job at tidying up the hay in a haystack, than finding needles in it. Usually, additional modules are associated with the SIEM, among them the UBA, and those are indeed the ones that find the needle.
Bonus: What is SOAR?
Security management is not just about threat detection. Security analysts and incident response teams still need to respond to the incidents they have discovered, and that is where SOAR comes in. Depending on who you ask, SOAR can stand for a multitude of things, but two of the most common definitions are:
- SOAR: Security Operations, Analytics and Reporting;
- SOAR: Security Orchestration and Automated Response.
This category of solutions is also sometimes called:
- SOAP: Security Orchestration and Automation Platform;
- Incident Response Automation;
- Orchestration and Response Automation.
Regardless of what it means, SOAR products are all about using automation to help reduce response times, improve consistency and increase the productivity of incident response teams. Three of the key features that enable these incident response productivity gains are:
- Incident Management – This resource may also be referred to as ticketing or case management. Incident Management helps organize incident response efforts by assigning owners to incidents, tracking the status and priorities of the investigation, as well as providing a centralized system to collect and work with the evidence.
- Security Orchestration – Orchestration tools typically use pre-built bi-directional APIs to connect and coordinate multiple security solutions and IT infrastructure. These APIs make it easier to acquire information from other systems as well as perform actions on those systems. For example, orchestration can be used to programmatically obtain IP reputation information or adjust the rules of a firewall.
- Response PlayBooks – PlayBooks take orchestration to high speed. They logically group many actions from different systems to accomplish specific tasks, such as investigation, containment or remediation.
For example, it is possible to have a PlayBook that performs the following actions on multiple systems with a single click of a button:
- Removes all emails received by a user at the time of infection (e.g. from an email server);
- Analyzes the emails to extract URLs and attachments;
- Extracts the attachments in a Sandbox (e.g. Check Point Sandblast or other);
- Gets the URL reputations with a reputation service (e.g. Cisco Umbrella);
- Geolocates any network connections made by the attachments in the Sandbox with a geolocation service (e.g. Maxmind);
- Uses AI to determine if any of the emails are phishing, based on the information in steps 1 to 5 above;
- Searches a SIEM / LMS for other users who received the same emails (e.g. Splunk, QRadar or Darktrace).
Conclusion
In the current cybersecurity context, it is essential to implement a Security Operations Center (SOC), equipped with tools that allow visibility of all its assets in real-time.
This makes it possible to analyse and respond to security incidents, with analysis engines based on artificial intelligence, such as UEBA, that contribute to the reduction of false positives, as well as, to the increase of detection capacity and incident response.
As specialists in this area, with experience in implementing the best cybersecurity solutions in the market, we are available to provide solutions that respond to the above-mentioned needs, appropriate to the context of each corporate environment.