SOC is a combination of people, processes, and technology in a centralized area responsible for monitoring and analyzing an organization’s security posture. The main objective of a SOC is to detect, investigate and respond to cybersecurity threats in a timely and effective manner. SOCs typically use a mixture of security tools and techniques, such as penetration detection systems, firewall logs, and security information and event management systems (SIEM), to monitor the organization’s network and systems for potential security breaches. The SOC team is also responsible for incident response, which includes containing and mitigating the impact of security incidents, and identifying and addressing the root cause of security breaches.
SOC brings several advantages to your business, including:
- Increased visibility and control: SOC provides a centralized view of an organization’s security posture, which allows security teams to better understand the threats they face and take appropriate action to mitigate them.
- Improved threat detection and response: SOC uses a combination of security tools and techniques to monitor an organization’s network and systems for potential security breaches, enabling them to detect and respond to threats quickly and effectively.
- Compliance: SOC helps organizations meet compliance and regulatory requirements such as those related to data privacy and security.
- Cost reduction: Having a SOC can potentially reduce costs associated with security breaches, such as those related to data recovery, legal fees, and lost productivity.
- Continuous improvement: The SOC can continuously monitor, assess, and improve the organization’s security posture using machine learning and artificial intelligence.
- Collaboration: The SOC brings together multiple teams such as security, IT and business that work together to handle security incidents.
How does the SOC work?
The SOC serves as an intelligence hub for the enterprise, receiving real-time activity logs from all networks, servers, endpoints and other digital assets in the organization and uses intelligent automation to identify, prioritize and respond to potential cybersecurity threats.
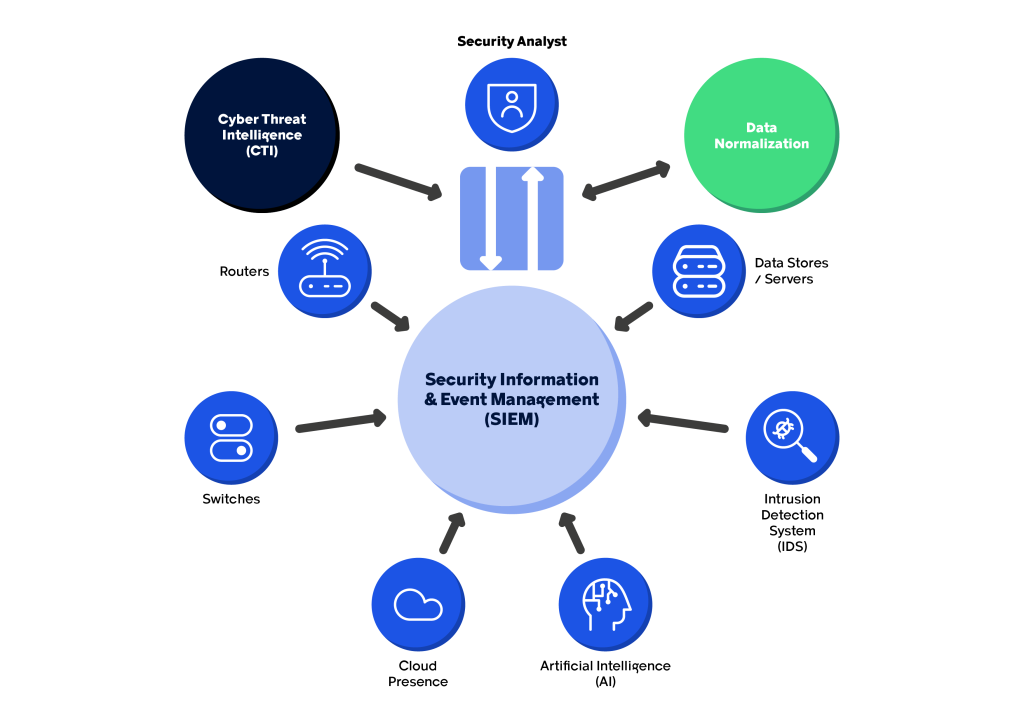
Figure 1 provides an abstract view of what happens in a SOC.
How New Cognito’s SOC can help your organization.
- Permanent network monitoring that gives complete visibility to digital activity and detects anomalies.
- Mitigate risks and ensure compliance with existing national regulatory entities.
- Threat detection and intelligence capabilities that assess the source, impact and severity of each cyber security incident.
- Decisive incident response and remediation through a mix of automated technologies, processes and people.
- Reporting to ensure that all incidents and threats are entered into the data repository, making it more accurate and responsive in the future.
- Ensure security continues while your company is focused on the business
Conclusion
In summary, the SOC proactively protects all network devices that communicate with using Internet Protocol (IP), to which it has visibility. Without visibility of the devices control of them is difficult and there are likely to be blind spots that can be found and exploited by Hackers.
It is important to remember that the big goal of the SOC is not only to get a complete view of the business threat landscape, including not only the various types of endpoints, servers and software on premises, but also third-party services and the traffic that flows between them.